List and Briefly Define Three Classes of Intruders
Do the following review questions in a paragraph in a word document. 115 What metrics are useful for profile-based.
The three classes of intruders are.
. An individual who is not authorized to use the computer and who penetrates a systems access controls to exploit a legitimate users account. An individual who is not authorized to use the computer. 114 What is the difference between statistical anomaly detection and rule-based intrusion detection.
We have qualified writers holding bachelors graduate and Doctoral certificates matched with skill and expertise. 111 List and briefly define three classes of intruders. 111 List and briefly define three classes of intruders.
From simple essay plans through to full dissertations you can guarantee we have a service perfectly matched to your needs. 112 What are two common techniques used to protect a password file. 114 What is the difference between statistical anomaly detection and rule-based intrusion detection.
112 What are two common techniques used to protect a password file. 114 What is the difference between statistical anomaly detection and rule-based intrusion. 113 What are three benefits that can be provided by an intrusion detection system.
114 What is the difference between statistical anomaly detection and rule-based intrusion detection. List and briefly define three classes of intruders. No plagiarism is very important.
Classes of Intruders Assignment List and briefly define three classes of intruders. Terms in this set 13 List and briefly define three classes of intruders. List and briefly define three classes of intruders.
I was bombarding him with fine tuning and he handled it professionally. 114 What is the difference between statistical anomaly detection and rule-based intrusion detection. 111 List and briefly define three classes of intruders.
Three Classes of Intruder. Masquerader misfeasor and clandestine user. 112 What are two common techniques used to protect a password file.
What are the two ways used for protecting a passwordfile. Three Classes of Intruders Masquerader unauthorized user who penetrates a system exploiting a legitimate users account outside Misfeasor - legitimate user who makes unauthorized accesses or misuses his privileges inside Clandestine user - seizes supervisory control to evade auditing and. List and briefly define three classes of intruders.
Masquerader - an individual usually and outsider who pretends to be a legitimate user but they are no View the full answer. 112 What are two common techniques used to protect a password file. List and briefly define three classes of intruders Answer the following question.
Masquerader is an external user who is not authorized to use a computer and yet tries to gain privileges to access a legitimate users account. List and briefly define categories of security services. An individual who is not authorized to use the computer and who penetrates a systems access controls to exploit a legitimate users account.
Our academic experts are ready and waiting to assist with any writing project you may have. 112 What are two common techniques used to protect a password file. 111 List and briefly define three classes of intruders.
113 What are three benefits that can be provided by an intrusion detection system. 113 What are three benefits that can be provided by an intrusion detection system. A legitimate user who accesses data programs or resources for which such access is not authorized or who is.
111 List and briefly define three classes of intruders. 111 List and briefly define three classes of intruders. 112 What are two common techniques used to protect a password file.
One of the two most publicized threats to security is the intruder the other is viruses generally referred to as a hacker or cracker. Give examples of metrics that are useful forprofile-based intrusion. Give examples of intrusion.
A legitimate user who accesses data programs or resources for which such access is not authorized or who is authorized. List and briefly define three classes of intruders. 113 What are three benefits that can be provided by an.
115 What metrics are useful for profile-based. List and briefly define three classes of intruders. 81 List and briefly define three classes of intruders.
List and briefly define three classes of intruders. List and briefly define three classes of intruders. List and briefly define three classes of intruders Writing Services Article writing Case Study writing Coursework writing Creative writing Custom Essay writing Dissertation writing Essay writing Homework writing Paper writing Presentation writing Report writing.
113 What are three benefits that can be provided by an intrusion detection system. A legitimate user who accesses data programs or. List and briefly define categories of security mechanisms 10 marks Q3.
112 What are two common techniques used to protect a password file. List and briefly define three intruder behavior patterns. Terms in this set 7 81 List and briefly define three classes of intruders.
Thank you I will hire again the writer. 113 What are three benefits that can be provided by an intrusion detection system. In an important early study of intrusion Anderson ANDE80 identified three classes of intruders.
What is the role of compression in the operation of a virus. Chapter 8 - Intrusion Deection. What are the essentials ingredients of a symmetric cipher.
112 What are two common techniques used to protect a password file. 111 List and briefly define three classes of intruders. 113 What are three benefits that can be provided by an intrusion detection system.
Explain how statistical anomaly detection and rule-basedintrusion detection are used to detect different types of intruders.
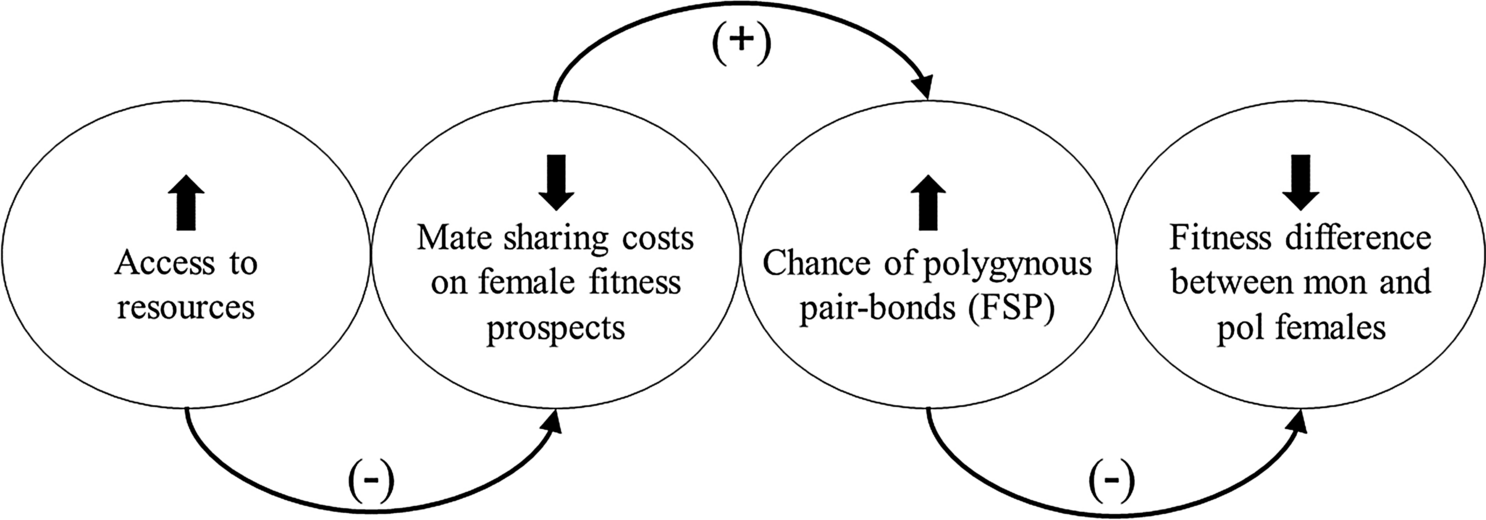
High Frequency Of Social Polygyny Reveals Little Costs For Females In A Songbird Scientific Reports
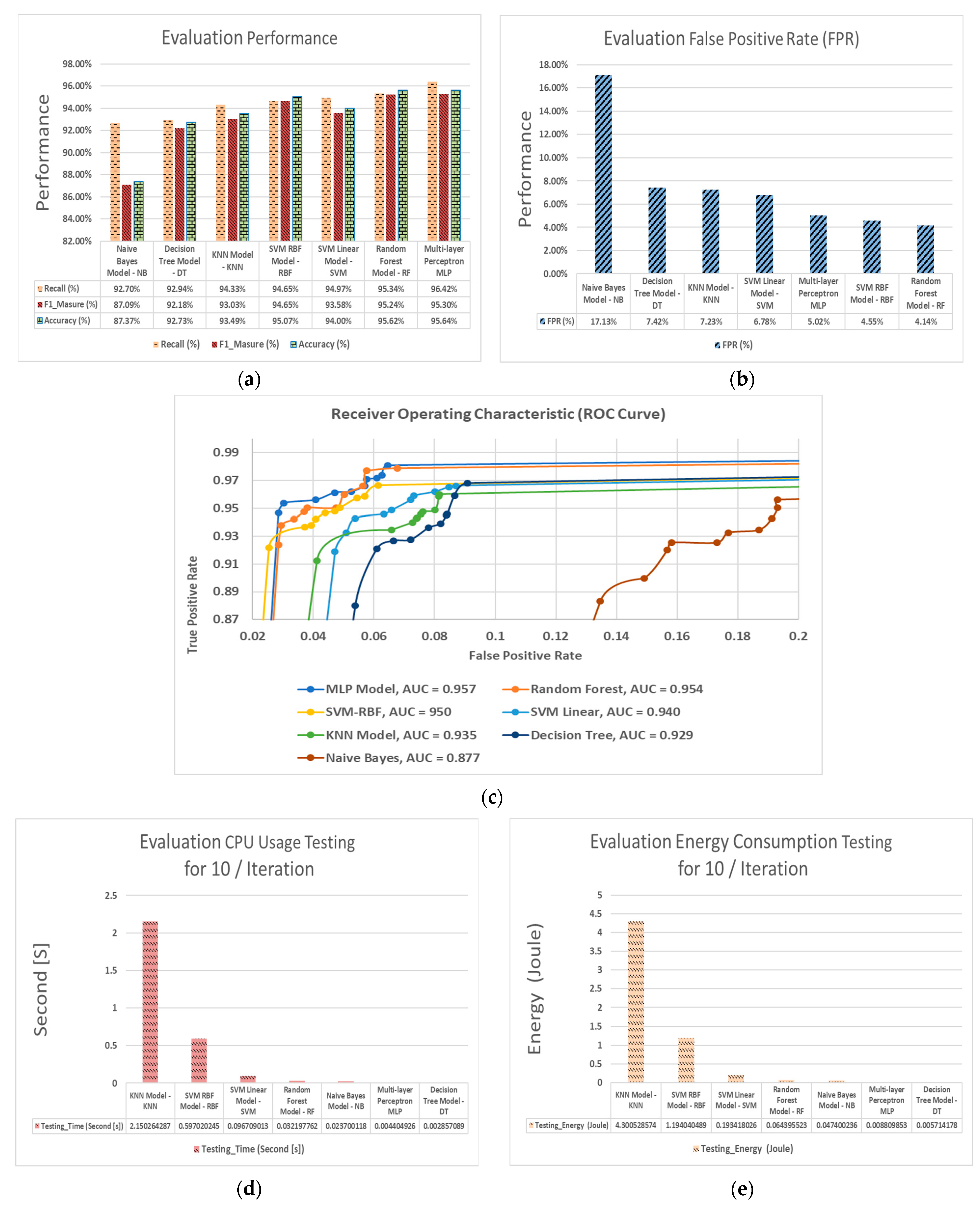
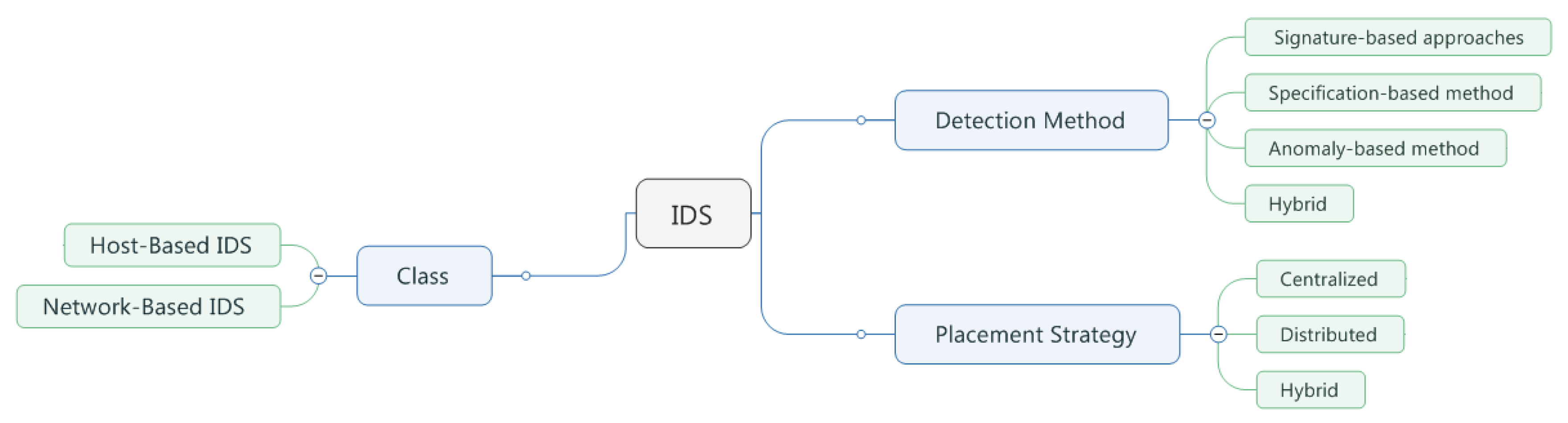
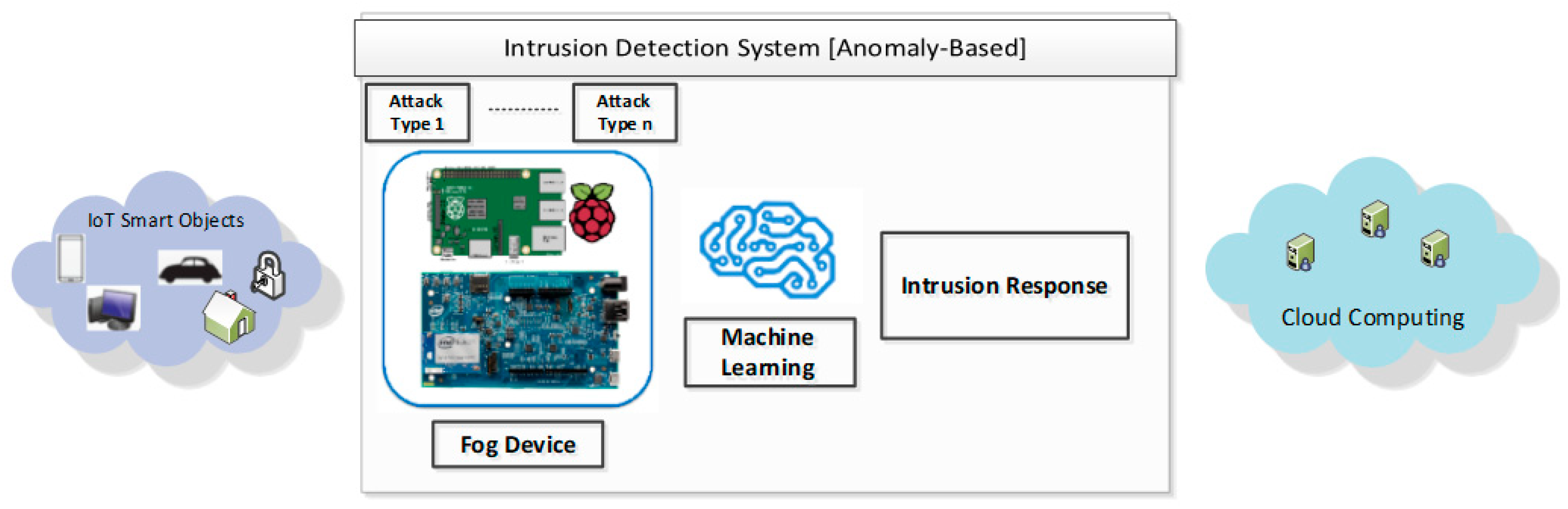
Electronics Free Full Text Classifier Performance Evaluation For Lightweight Ids Using Fog Computing In Iot Security Html
Electronics Free Full Text Classifier Performance Evaluation For Lightweight Ids Using Fog Computing In Iot Security Html
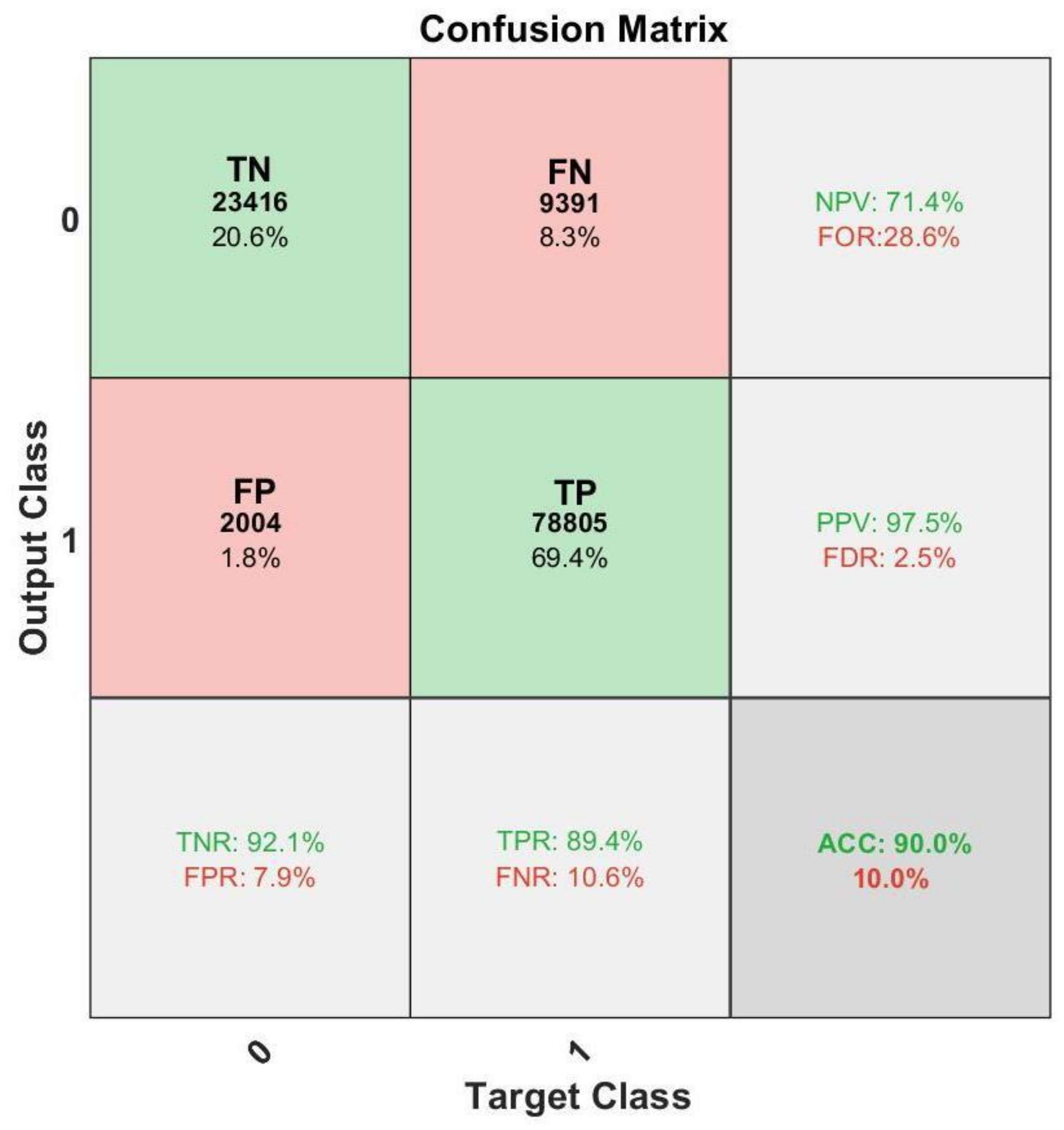
Drones Free Full Text A Multifractal Analysis And Machine Learning Based Intrusion Detection System With An Application In A Uas Radar System Html
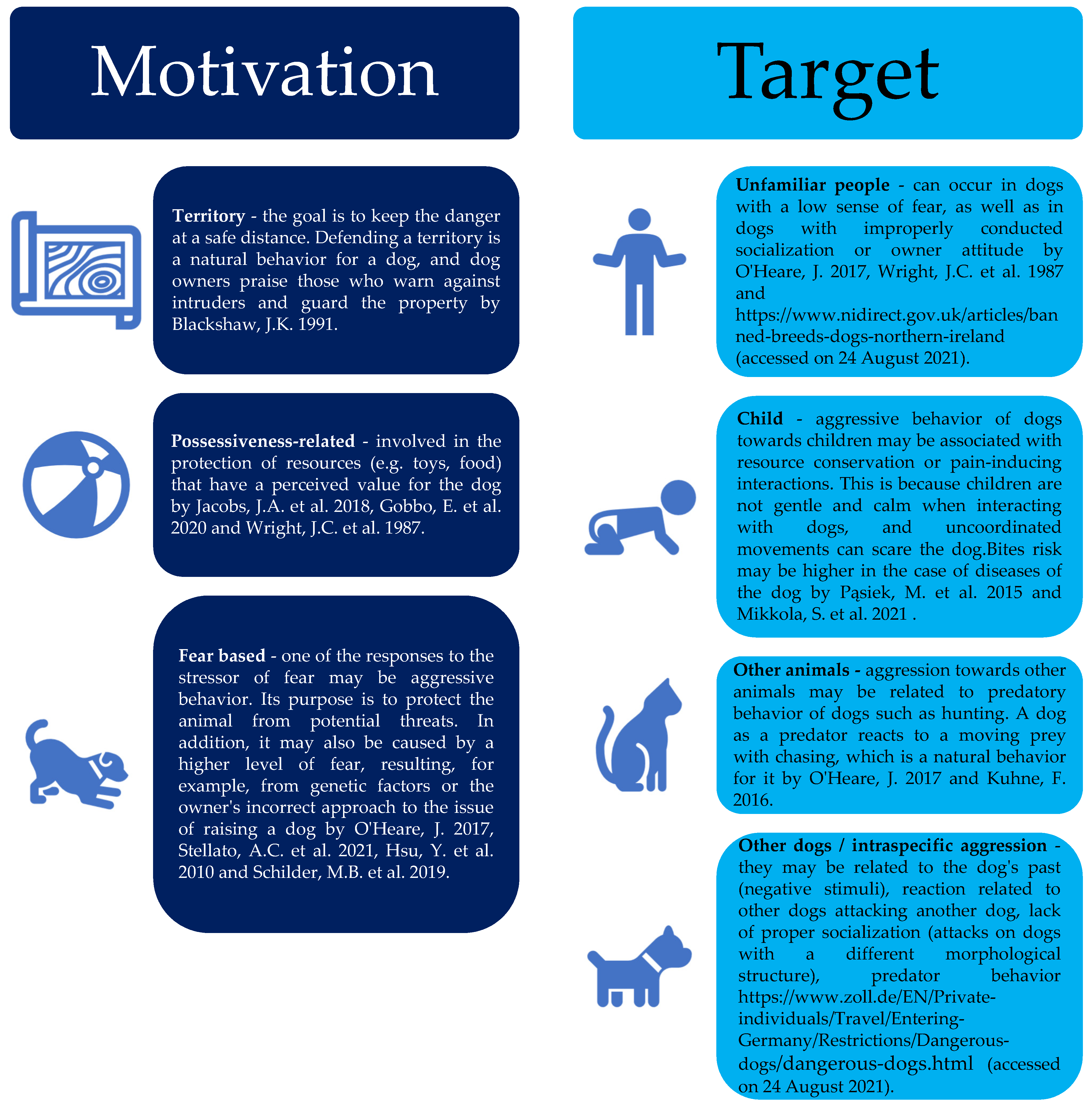
Animals Free Full Text Review On Selected Aggression Causes And The Role Of Neurocognitive Science In The Diagnosis Html
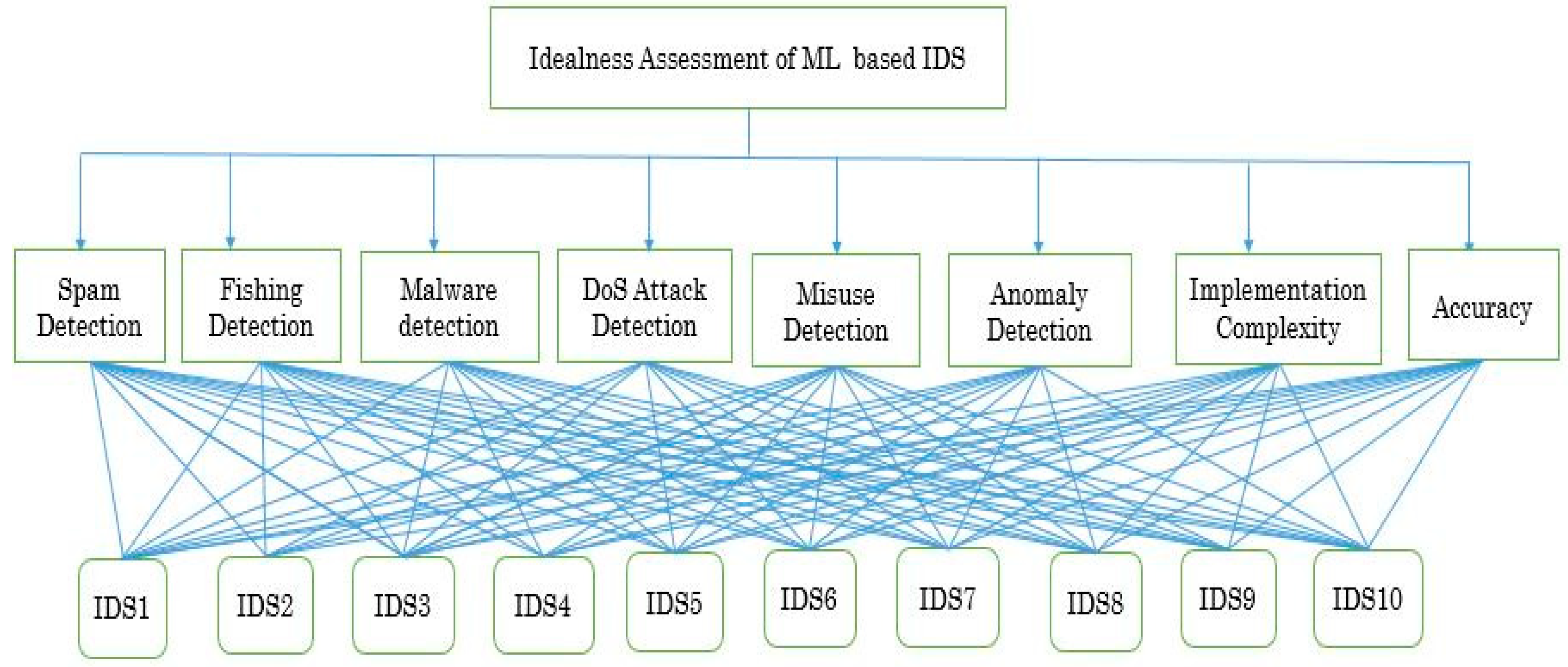
Sustainability Free Full Text Analyzing The Impact Of Cyber Security Related Attributes For Intrusion Detection Systems Html

Chapter 9 Bugs And Security Holes Two Dangers Of Informatics Cairn International Edition

Pdf A Framework For Malicious Traffic Detection In Iot Healthcare Environment
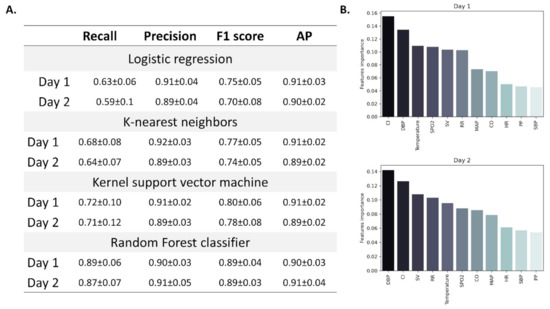
Jcm November 1 2021 Browse Articles

Pdf On Generating Network Traffic Datasets With Synthetic Attacks For Intrusion Detection
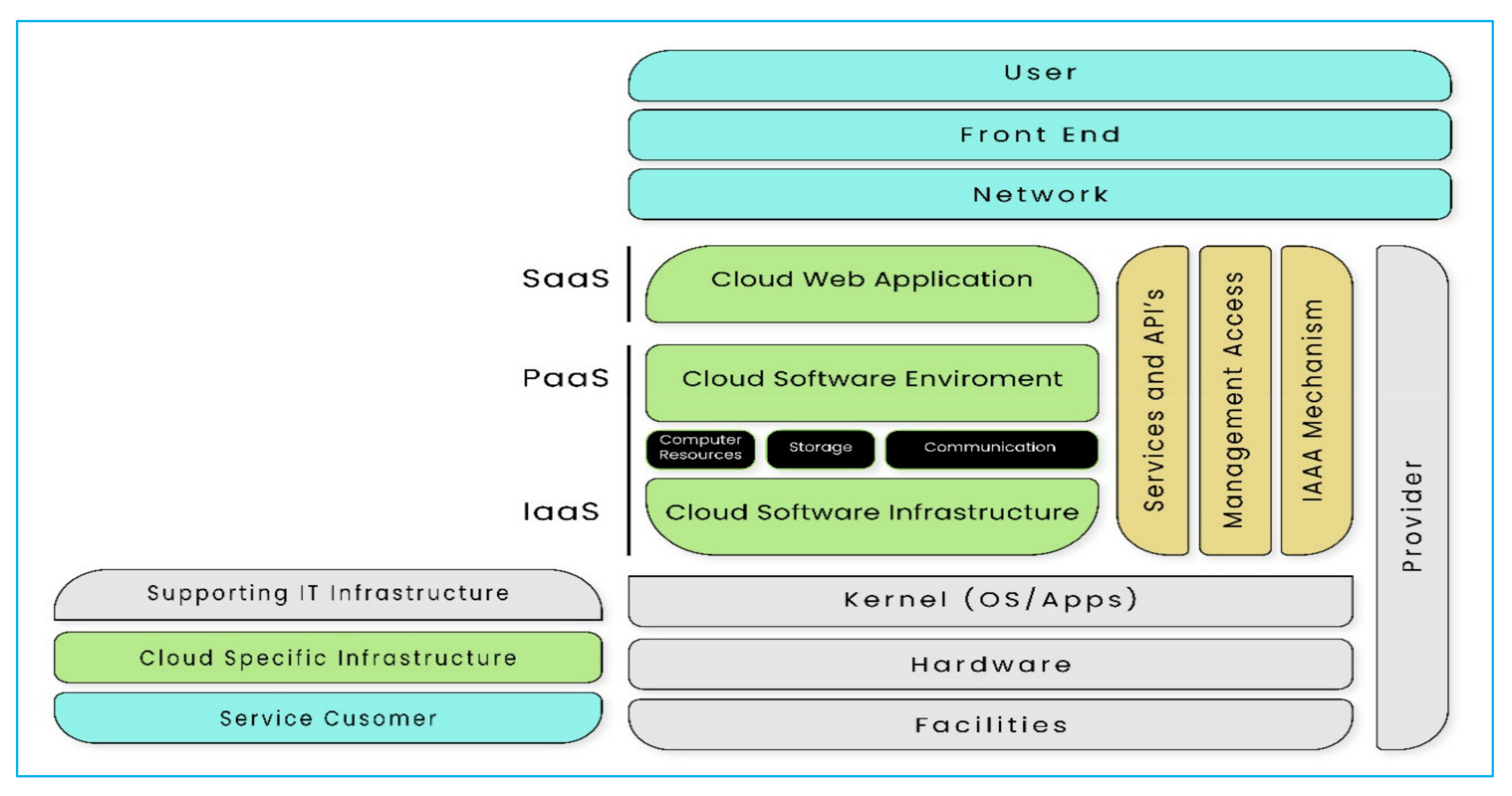
Electronics Free Full Text Next Generation Blockchain Enabled Virtualized Cloud Security Solutions Review And Open Challenges Html
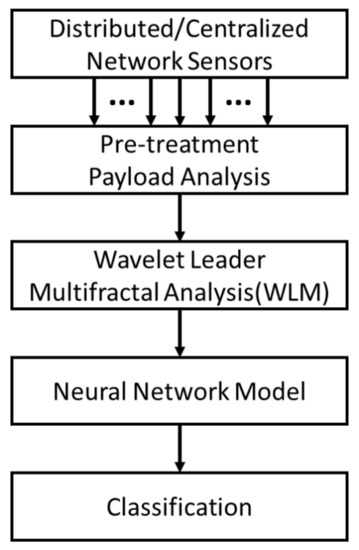
Drones Free Full Text A Multifractal Analysis And Machine Learning Based Intrusion Detection System With An Application In A Uas Radar System Html
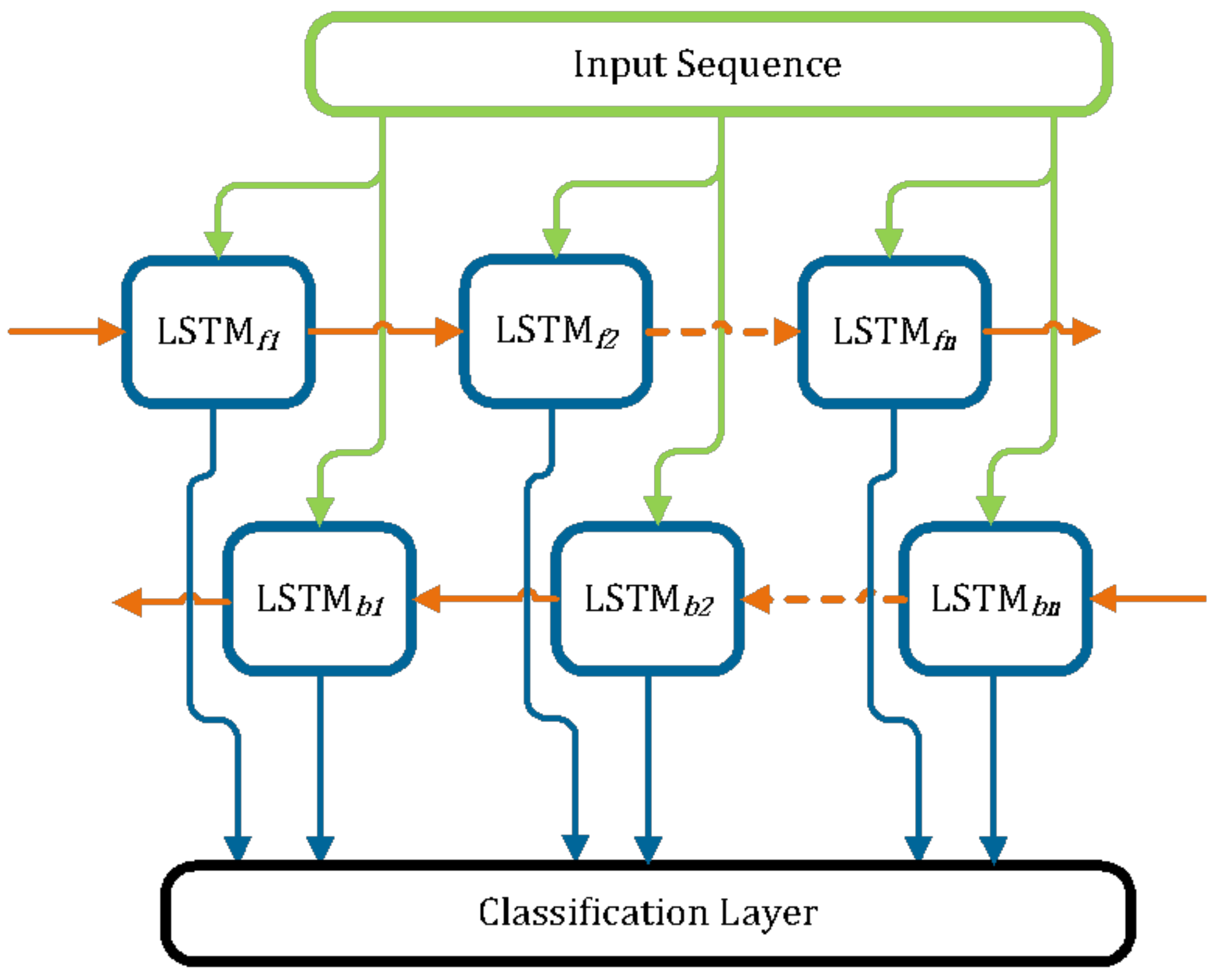
Drones Free Full Text A Multifractal Analysis And Machine Learning Based Intrusion Detection System With An Application In A Uas Radar System Html

Electronics Free Full Text Intrusion Detection System For The Internet Of Things Based On Blockchain And Multi Agent Systems Html
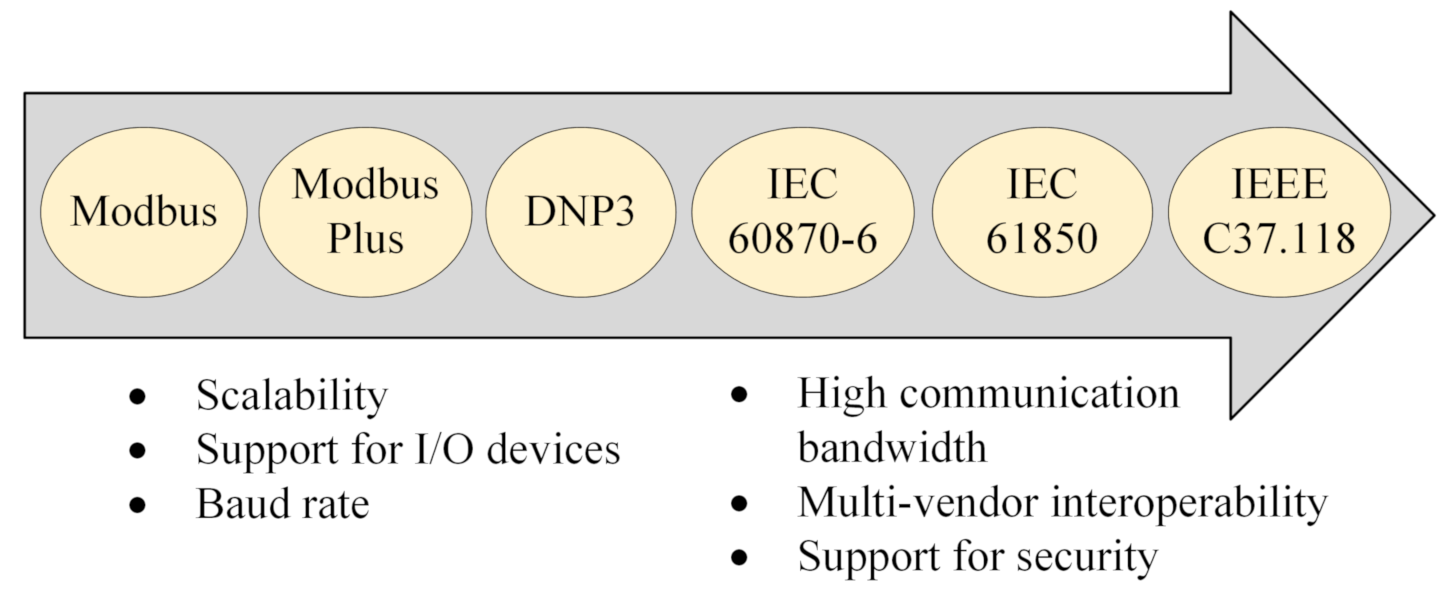
Sensors Free Full Text Vulnerability And Impact Analysis Of The Iec 61850 Goose Protocol In The Smart Grid Html


Comments
Post a Comment